Are you looking for my non-technical blog?
30 September 2005
Homepages Are Dead, Long Live The Blogs *
However homepages still excels the blogs in their organization, they can be organized by links and menus and not by date like blogs, and that's why it is still used in professional fields like companies sites, and online news sites, etc as information can be sorted by categories and organized in different menus. But will this continue to be true in the near future? O.K. Google's point of view is "Why sort your stuff, where you can search for them", and you may notice this in your Gmail account, where you cannot organize your mails into folders as you can just leave them as they are, and then search for the mail you want any time. And that's why I think that the lack of organization of the blogs will not be a problem anymore as long as they are searchable and indexed by searching engines. I also expect the blog hosting sites to have search plugins on the near future to be added to the blogs there. Finally, will there be someday where there will be "http://microsoft.blogspot.com", "cnn.blogspot.com", and "otlob.blogspot.com"!?
* The title of this article is inspired by Gartner's article; "Intrusion Detection Is Dead, Long Live The Intrusion Prevention"
Tags: Internet, Blog, Web, Writers, Gr33n Data
Spanish Arabic Connection
aceite — oil Alá — Allah alberca — tank, swimming pool alcade — mayor alcohol — alcohol aldea — village (same source as English word "alderman") algarroba — carob algodón — cotton algoritmo — algorithm alkimia — alchemy almohada — pillow alquiler — rent arroz — rice asesino — assassin atún — tuna ayatolá — ayatollah azafrán — saffron azúcar — sugar baño — bathroom berenjena — eggplant Corán — Koran cuzcuz — couscous espinaca — spinach fulano — what's-his-name gacela — gazelle guitarra — guitar hachís — hashish hasta — until imán — imam islam — Islam jaque — check (in chess) jaque mate — checkmate jirafa — giraffe limón — lemon mezquita — mosque momia — mummy muslim — muslim ojalá — I hope, God willing olé — bravo ramadán — Ramadan rehén — hostage rincón — corner, nook
Blog Honeypot
It's still 3:09 P.M.
29 September 2005
28 September 2005
Rest of The World
27 September 2005
Code Masturbation
Opera is now Free
The makers of the Opera Web browser has decided to make their product completely free - like Linus Trovalds the creator of Linux sait, "Software is like sex, it is supposed to be free" - and to remove the banner ads from its browser altogether. I’ve never been a huge Opera fan, but it’s known to be very rich features wise, but also comes with a slightly more complicated Interface than Firefox or IE. Obviously this move was inevitable, as Firefox is stealing the lights, and Opera is barely profiting from the Ads or the browser in the first place, as it controls only around 1% of the marketshare. If Opera browser is to gain more momentum it will have to be free.
Source: http://www.technoogle.com/
GeoURL
Happy Birthday Google
26 September 2005
Basic NetScreen Firewall Configuration
You first need a console and the default username and password are "netscreen"/"netscreen". Then you have to determine if you are going to install it in Layer-II mode or LayerIII. We are going to consider the Layer-II (Transparent) mode configuration.
First, put all the interfaces in Layer-II zones (V1-Trust, V1-Untrust, V1-DMZ)
set interface [interface-name] zone [zone-name]Then configure an IP address to VLAN1 interface (The management interface in case of Transparent mode operation)
Eg. set interface e1 zone V1-Trust
set interface vlan1 ip [ip-address]/[subnet-mask]Now after adding the interfaces to different zones, there must be policies in order to allow traffic to cross the different zones ... policies is how you are going to decide who is allowed to communicate with who and with whcih TCP/UDP services
Eg. set interface vlan1 ip 10.0.0.1/24
set police from [source-zone] to [destination-zone] [src-ip] [dst-ip] [service] {permit|deny} [log]Network Configuration
Eg. set policy from V1-Trust to V1-Untrust 10.0.0.10 10.0.0.2 FTP permit
PC2: 10.0.0.2/24 (V1-Untrust)
VLAN1: 10.0.0.1/24
[PC1]------------[Firewall]------------[PC2]
Notes:
- In Transparent mode the firewall acts as a bridge in the way the traffic is forwarded, so it is normal for the hosts connected to the different interfaces to have IP addresses from the same subnet.
- The default behavior of the firewall is to block traffic between different zones, so you have to create policies in order to path traffic. However this default can be changed.
IBM G40 Auto Update
25 September 2005
Ten Years Puzzle
24 September 2005
Selective Blindness
Cross Site Scripting - XSS
*** FIXME *** Cross Site Scripting (XSS): Is one of code injection attacks where the attacker inserts some code (or data in general) in a web server in order for that web server (or the victim's web browser) to show or execute that inserted data. *** FIXME ***.There are three different types of XSS attacks according to wikipedia; however I am going to talk about the third type (Type number 2) here as it is the most interesting and dangerous.
Imagine a web forum where different users can post articles and comments etc. So an attacker can forge his post to contain some HTML tags or JavaScript in stead of clear text. So the result will be the execution of that HTML tags or JavaScript in the other forum visitors' browsers. This can be some HTML tag to redirect users to his own web page, or a JavaScript that can display an annoying message, steal the users session-ID (their logging to that forum), pop-up some window asking them about some info and then sending this info (like credit card number, email address, etc.) to some remote location.
This attack is not limited to web forums only as it can target any sites that takes input from users and displays this input later like blog comments, movies reviews, online web chatting systems, online computer games, etc. Emails can also carry such attacks but it may be called phishing, or Email fraud then.
Many solutions have been used in order to stop such attacks like disabling HTML tags or converting them to normal text before displaying them. Some forums use their own limited tags like [link:"http://www.linux.org"] or [b] and [/b] etc.
23 September 2005
Block-Checker Removal
- Press ctrl+alt+del then choose processes tab and end the "block-checker" process.
- Go to the block checker folder( e.g. c:\program files\block-cheker) and delete the folder.
- Go to run > type regedit > press F3 and find every record with the name "blockcheck" and delete it (This step is optional)
22 September 2005
Fanoos Ramadan
 Fanoos Ramadan or Ramadan's Lamp is one of the Egyptian traditions however it is known in many other Islamic countries now. The tradition started in the year 358 AH (Hijri) on the 15th of Ramadan when the Fatimi leader El Mo'ez Le Deen Allah enered Egypt, and the Egyptians recieved him with lamps and torches. And since then the Fanoos has been known as one of the main symbols of Ramadan and most of the people own it and light it in Ramadan, especially children. There has been also varios songs related to Ramadan talking about the Fanoos and the Mesaharaty - some one who wakes people up at night in order to eat before fasting. The tradition fanoos contained a candle in it, while today's ones have different shapes and using battries and LED's instead of candles.
Fanoos Ramadan or Ramadan's Lamp is one of the Egyptian traditions however it is known in many other Islamic countries now. The tradition started in the year 358 AH (Hijri) on the 15th of Ramadan when the Fatimi leader El Mo'ez Le Deen Allah enered Egypt, and the Egyptians recieved him with lamps and torches. And since then the Fanoos has been known as one of the main symbols of Ramadan and most of the people own it and light it in Ramadan, especially children. There has been also varios songs related to Ramadan talking about the Fanoos and the Mesaharaty - some one who wakes people up at night in order to eat before fasting. The tradition fanoos contained a candle in it, while today's ones have different shapes and using battries and LED's instead of candles.
Red Eye
19 September 2005
Manalaa Upgraded
17 September 2005
Hectoblog
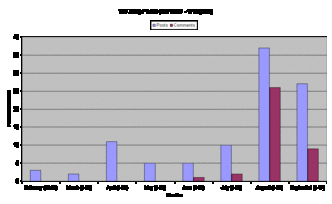 *** Click on image to enlarge ***
*** Click on image to enlarge ***
|
- February: 3 Posts (0 comments)
- March: 2 Posts (0 Comments)
- April: 11 Posts (0 Comments)
- May: 5 Posts (0 Comments)
- June: 5 Posts (1 Comment)
- July: 10 Posts (2 Comments)
- August: 37 Posts (26 Comments)
- September: 27 Posts (9 Comments)
- Total: 100 Posts (38 Comments)
Which Religion Is The Right One For Me?
You scored as Islam. Your beliefs are most similar to those of Islam. Do more research on Islam and possibly consider taking the shahadah and officially becoming a Muslim, if you aren't already.
Despite the actions of some - who go against the teachings of Islam - Islam is a religion of peace; the word "islam" means "peace through submission to God." "Muslim" means "one who submits to God." Islam is the third of the three Abrahamic faiths, and it shares much with Judaism in Christianity; its differences are the acceptance of Muhammad as the last and final prophet, and the oneness of God - in other words, that Jesus, though he was a revered prophet, was not in fact God, and only one God exists. Apparently the Taliban could not read (though their name means "students"), because the Qur'an states that men and women are equal as believers, and that all believers should be educated and seek knowledge. Modesty in dress and behavior is required in Islam for both men and women to preserve the values of society and move the emphasis from superificial appearance to intelligence, knowledge, and God.
|
16 September 2005
Internet Exploder
Paris Hilton Hacker Sent To Jail
Visiting Egypt
Rainbow - Qous Qazah [Arabic]
 This was the first time to see a real rainbow in the sky. It may no be that clear photo, however I like the scene of the rainbow colours surrounded by dark clouds.
January, 2004
This was the first time to see a real rainbow in the sky. It may no be that clear photo, however I like the scene of the rainbow colours surrounded by dark clouds.
January, 2004
15 September 2005
One Hundred Kisses
Dear Sweet Heart, I can't send my salary this month, so I am sending 100 kisses. Your HubbyHis wife replied back after some days to her husband:
Dearest Hubby, Thanks for your 100 kisses, I am sending the expenses details.Please don't worry for me, I have balance 35 kisses and I hope I can complete this month. Shall I plan same way for next months, Please advise?
- Milk man agreed on 2 kisses.
- Teacher agreed on 7 kisses.
- Our house owner is coming every day and taking two or three kisses of mine.
- Vegetable and food shop keeper did not agree on kisses only, so I have given some other items to him.
- Others 40 kisses
14 September 2005
Egyptian Metal
Manalaa Algorithm
13 September 2005
Blog Patrol Crack
12 September 2005
Nice Article About OOP
Blog Social Engineering
In the field of computer security, social engineering is the practice of obtaining confidential information by manipulation of legitimate users. A social engineer will commonly use the telephone or Internet to trick people into revealing sensitive information or getting them to do something that is against typical policies. By this method, social engineers exploit the natural tendency of a person to trust his or her word, rather than exploiting computer security holes. It is generally agreed upon that “users are the weak link” in security and this principle is what makes social engineering possible. WikipediaSo, It's not recommended to put many personal information on your blog as malicious users may extract these information in order to attack you. People sometimes forget that others are reading their blogs and begin to write stuff that the others are not supposed to know about them. Imagine the that you are writing in your blog how you have successfully configured you XYZ ADSL modem and showing people the configuration you are using in order to HELP them configure their simillar CPE's. It is really very nice idea, but did you check this configuration first to see if it doesn't contain IP addresses or clear-text password.
eBay Bought Skype
Just 4 Years
07 September 2005
Kazaa Under Arrest
04 September 2005
Words of Wisdom
03 September 2005
I Am The Master Of My Fate
Know Who Links To You
link:gr33ndata.blogspot.comDon't forget to replace "gr33ndara.blogspot.com" by your actual blog URL.
02 September 2005
Does Google Like You !?
Link To Us
< a href= "http://gr33ndata.blogspot.com/" > < img src= "http://www.geocities.com/gr33ndata/blogfilez/banner_gr33ndata.jpg" > < /a >Kelmeteen Banner:
< a href= "http://kelmeteen.blogspot.com/" > < img src= "http://www.geocities.com/gr33ndata/blogfilez/banner_kelmeteen.jpg" > < /a >
Spammers Are Here
Alexandria Corniche
 Alexandria is the chief seaport in Egypt, and the country's second largest city. It is Located on the Mediterranean Sea coast.
Alexandria is the chief seaport in Egypt, and the country's second largest city. It is Located on the Mediterranean Sea coast.







