This actually works. It will not crash your computer, it just breaks Notepad in that it causes it to display very oddly. No perm damage comes of the following steps.
Here's how to do it:
1. Open up Notepad (not Wordpad, not Word or any other word processor)
2. Type in this sentence exactly (without quotes): "this app can break"
3. Save the file to your hard drive.
4. Close Notepad
5. Open the saved file by double clicking it.
Instead of seeing your sentence, you should see a series of squares. For whatever reason, Notepad can't figure out what to do with that series of characters and breaks.
Sourece: Helpero dot Com
Tags: Windows, Notepad, Gr33n Data
Are you looking for my non-technical blog?
This is now my technical-only blog, my non-technical blog is here.
31 July 2006
Time to Kiss the U.N. Goodbye
I think it's time to kiss the U.N. (United Nations) goodbye. The organization has failed to resolve many issues lately. Actually, the idea of some specific countries having the right to block any Securiy Council resolution, by using their Veto right, is totally unacceptable and doesn't make any sense. It's really funny that the United States has used its Veto power 13 times, 11 of them were to protect Israel. I think the only solution for this situation, is by forming a parallel organization with more appropriate rules, and ask the countries in the whole world to join it and leave the UN with it's weird rules. I think the Arab countries may make such initiative, and gather as much members as they can.
Tags: UN, Veto, Gr33n Data
Tags: UN, Veto, Gr33n Data
Mel Gibson: The Jews are Responsible for All The Wars in The World
By the time "The Passion of the Christ" opened in February 2004, the liberal media had been accusing Mel Gibson for almost a year of promoting anti-Semitism. Gibson's controversial movie showed Jews torturing Jesus Christ, then killing him.
On July 29, it's been reported that Mel Gibson has been arrested for drinking while driving. According to the report, in addition to threatening the arresting deputy and trying to escape, Gibson said, "The Jews are responsible for all the wars in the world" .
Gibson has apologized for his behavior, however there is a huge debate now about his future in Hollywood, after his anti-Semitic remarks.
I myself feel that there is a link between the two events, remember that Gibson has a movie called "Conspiracy Theory", and there may be some Conspiracy right here as well. Let me ask, why it is not accepted to criticize the Jews, what's so special about them!? Isn't it Ironic (like Alanis Morissette's song), that it is not accepted to say such thing about Jews or Israel, however it is ok for Israel to continue murdering the Lebanese civilians (mostly children) for about 20 days!? By the way, Israel has just committed another massacre today in Qana. Finally, after seeing the Israeli deeds in Lebanon, I think Gibson had the some point in saying what he said.
Tags: Mel Gibson, Jews, Gr33n Data
On July 29, it's been reported that Mel Gibson has been arrested for drinking while driving. According to the report, in addition to threatening the arresting deputy and trying to escape, Gibson said, "The Jews are responsible for all the wars in the world" .
Gibson has apologized for his behavior, however there is a huge debate now about his future in Hollywood, after his anti-Semitic remarks.
I myself feel that there is a link between the two events, remember that Gibson has a movie called "Conspiracy Theory", and there may be some Conspiracy right here as well. Let me ask, why it is not accepted to criticize the Jews, what's so special about them!? Isn't it Ironic (like Alanis Morissette's song), that it is not accepted to say such thing about Jews or Israel, however it is ok for Israel to continue murdering the Lebanese civilians (mostly children) for about 20 days!? By the way, Israel has just committed another massacre today in Qana. Finally, after seeing the Israeli deeds in Lebanon, I think Gibson had the some point in saying what he said.
Tags: Mel Gibson, Jews, Gr33n Data
The Massacre of Qana




And this is how the Israeli pigs defend themselves. By killing children and disabled's. Thank you Mr. Bush for giving Israel the right to defend itself this way.
Tags: Lebanon, Israel, Gr33n Data
30 July 2006
Qana Once More
 "More than 40 people, including 20 children, have been killed in an Israeli air strike on the southern Lebanese town of Qana today. Qana was the site of an Israeli bombing of a UN base in 1996 that killed more than 100 people sheltering there during Israel's (Grapes of Wrath) offensive, which was also aimed at destroying Hezbollah", BBC News
"More than 40 people, including 20 children, have been killed in an Israeli air strike on the southern Lebanese town of Qana today. Qana was the site of an Israeli bombing of a UN base in 1996 that killed more than 100 people sheltering there during Israel's (Grapes of Wrath) offensive, which was also aimed at destroying Hezbollah", BBC NewsForgive my language, but Israel is a real mother fucker nation, and it's presence is simply against humanity. It's totally unacceptable to see a country committing those continuous massacres and crimes against humanity without being punished.
Tags: Lebanon, Israel, Qana, Massacre, Gr33n Data
28 July 2006
Google Announces Hosting for Open Source Projects
Google has created a repository system for software development much like SourceForge. The system even checks new project names against SourceForge's database to ensure no one sets up conflicting names.
Stein, an open source engineer with Google and chairman of the Apache Software Foundation, says, "We really like SourceForge, and we don't want to hurt SourceForge" or take away projects. Instead, Stein says that the goal is to see what Google can do with the Google infrastructure, to provide an alternative for open source projects.
Source: NewsForge.com
Tags: Google, Open Source, Gr33n Data
Stein, an open source engineer with Google and chairman of the Apache Software Foundation, says, "We really like SourceForge, and we don't want to hurt SourceForge" or take away projects. Instead, Stein says that the goal is to see what Google can do with the Google infrastructure, to provide an alternative for open source projects.
Source: NewsForge.com
Tags: Google, Open Source, Gr33n Data
27 July 2006
A Private Message to A Blogger
This is how to send a private message to a blogger whose Email address is not published in his/her profile. This may be useful in case you want to exchange Email addresses, however you do not want them to be shown to spammers, etc.
Most of the bloggers has the "Comment Notification Address" feature set in their blogs, it is an Email address, where you receive the contents of the new comments you receive on your own blog. So, you can now send a comment, and then delete it just after you send it. In such case it will obviously not be show, however it will be sent to the blog owner's Email.
Tags: Blog, Hack, Gr33n Data
Most of the bloggers has the "Comment Notification Address" feature set in their blogs, it is an Email address, where you receive the contents of the new comments you receive on your own blog. So, you can now send a comment, and then delete it just after you send it. In such case it will obviously not be show, however it will be sent to the blog owner's Email.
Tags: Blog, Hack, Gr33n Data
24 July 2006
Email Fraud
I received the follwing Email today:
Actually, I logged in there using a fake Email and password, and it seems that they've got real movies there, however I wanted to warn you in case you recieve simillar Emails. It seems that Scam, Spam, Fraud, Phishing, etc. are the hype of today. Finally, please think twice before entering your private data anywhere online.
Tags: Security, Email, Gr33n Data
مرحبا كيفك ان شاء الله تكون بخير حبيت ابلغك عن موقع افلام اكيد بيعجبك لانه جدا رائع ادخل عليه الان http://www.2flam.net وحط الايميل والباس الماسنجر لحتي تقدر تعمل دعوة لبيقت اصحابك الي بالايميل ونايس تايمThe message says, that you can download Arabic movies from this site, however in order to log in there, please use your Hotmail address and password as well :)
Actually, I logged in there using a fake Email and password, and it seems that they've got real movies there, however I wanted to warn you in case you recieve simillar Emails. It seems that Scam, Spam, Fraud, Phishing, etc. are the hype of today. Finally, please think twice before entering your private data anywhere online.
Tags: Security, Email, Gr33n Data
Lego Aircraft Carrier
So, you think you used to play with Lego when you were a kid? Now, think again.
URL: http://www.ezprezzo.com/crazypics/lego_aircraft_carrier.html
Tags: Lego, Toys, Gr33n Data
URL: http://www.ezprezzo.com/crazypics/lego_aircraft_carrier.html
Tags: Lego, Toys, Gr33n Data
Zune, MicroSoft's Reply to iPod
Microsoft has finally acknowledged one of the worst-kept secrets in the tech market in recent weeks: it is entering the handheld entertainment market with a device dubbed Zune, a music player and gaming device. It's long been suspected Microsoft was busy designing a potential "iPod killer," but details were slim to none.
Source: Internet News
According to Cesar Menendez, one of MicroSoft staff and Zune creators, Zune is Microsoft’s new, holistic approach to music and entertainment. And yes, this year, we’ll be releasing a device as part of the project. Under the Zune brand, we’re looking to build a community for connecting with folks, all to discover new music and entertainment.
Tags: Technology, Gadgets, Gr33n Data
Source: Internet News
According to Cesar Menendez, one of MicroSoft staff and Zune creators, Zune is Microsoft’s new, holistic approach to music and entertainment. And yes, this year, we’ll be releasing a device as part of the project. Under the Zune brand, we’re looking to build a community for connecting with folks, all to discover new music and entertainment.
Tags: Technology, Gadgets, Gr33n Data
Egyptian Chronicle
Todays blog is called Egyptian Chronicle, and as it name says, it is a mainly about Egyptian matters. The author of that blog calls herself Zenobia after the ancien Syrian queen who ruled from 267 to 272 A.D.
URL: http://egyptianchronicles.blogspot.com/
Tags: Egypt, Blog, Gr33n Data
URL: http://egyptianchronicles.blogspot.com/
Tags: Egypt, Blog, Gr33n Data
23 July 2006
Alarabiya and Google Earth
Alarabiya - The Arabic news channel - used Google Earth today in it's report about the Israeli attack on Lebanon. They were showing the battlefield and the various villages using the sattelita images stored in Google Earth software. Google's logo was shown on top of the screen as well.
Tags: Google, Alarabiya, Gr33n Data
Tags: Google, Alarabiya, Gr33n Data
22 July 2006
Estamos con Líbano

We are with Lebanon against the Israeli attack. [En]
Estamos con Líbano contra el ataque Israelí. [Es]
Nous sommes avec le Liban contre l'attaque Israélienne. [Fr]
Siamo con il Libano contro l'attacco Israeliano. [It]
Nós somos com o Líbano de encontro ao ataque Israeli. [Pg]
Tags: Lebanon, War, Gr33n Data
20 July 2006
From Israel to Lebanon


Monday, July 17, 2006: Kiryat shmona
Israeli girls write messages on a shell at a heavy artillery position firing into civilians inside Lebanon

Monday, July 17, 2006:
South Lebanon: A Lebanese Child Receiving the message from the Israeli girls!
Tags: Israel, Lebanon, Gr33n Data
19 July 2006
Better to Fight
"Better to fight for something than live for nothing", George S. Patton
Tags: Quotes, Fight, Gr33n Data
Tags: Quotes, Fight, Gr33n Data
18 July 2006
Hackers Learn from Open Source
Hackers are taking a page from the open-source playbook, using the same techniques that made Linux and Apache successes to improve their malicious software, according to McAfee Inc. "Over the last year and a half, we've noticed how bot development in particular has latched on to open-source tools and the open-source development model," he said. The current generation of bot software has grown to the point where open-source software development tools make a natural fit. With hundreds of source files now being managed, developers of the Agobot family of malware, for example, are using the open-source Concurrent Versions System (CVS) software to manage their project.
Mcafee researchers have described this use of open-source techniques in a new magazine set to be unveiled Monday. Called "Sage," the publication features a cover story entitled "Paying a price for the open-source advantage" in its inaugural issue. McAfee plans to publish Sage every six months, Marcus said.
Source: InfoWorld
Tags: Security, Open Source, Gr33n Data
Mcafee researchers have described this use of open-source techniques in a new magazine set to be unveiled Monday. Called "Sage," the publication features a cover story entitled "Paying a price for the open-source advantage" in its inaugural issue. McAfee plans to publish Sage every six months, Marcus said.
Source: InfoWorld
Tags: Security, Open Source, Gr33n Data
16 July 2006
Katyusha
Katyusha (Russian "Катюша") multiple rocket launchers were built and fielded by the Soviet Union in World War II. These launchers acquired this name, unofficial but immediately recognized in the Red Army, from the title of a popular Russian wartime song, "Katyusha". The song is about a girl longing for her beloved who is away from her while serving in the military. Katyusha is a tender Russian diminutive of a female name Ekaterina.
The term is now often used to describe small rocket artillery in general, whether they are Soviet-derived or originally built. Such rockets are often used in guerrilla warfare, for example by the National Front for the Liberation of Vietnam, Hezbollah, the Iraqi insurgency, and the Taliban.
Source: Wikipedia
Tags: Russia, Weapons, Gr33n Data
The term is now often used to describe small rocket artillery in general, whether they are Soviet-derived or originally built. Such rockets are often used in guerrilla warfare, for example by the National Front for the Liberation of Vietnam, Hezbollah, the Iraqi insurgency, and the Taliban.
Source: Wikipedia
Tags: Russia, Weapons, Gr33n Data
Israel Kills Lebanese Civilians
An Israeli air raid has killed at least 17 Lebanese civilians who were fleeing southern border areas. Women and children were among those killed when the convoy was hit. "Bodies litter the road," an eyewitness said.
Source: BBC News
Tags: Lebanon, Israel, Gr33n Data
Source: BBC News
Tags: Lebanon, Israel, Gr33n Data
Yersinia
Yersinia is a modular network tool designed to take advantage of some weakeness in different network protocols. Attacks for the following network protocols are implemented (but of course you are free for implementing new ones):
Tags: Network, Security, Gr33n Data
- Spanning Tree Protocol (STP).
- Cisco Discovery Protocol (CDP).
- Dynamic Trunking Protocol (DTP).
- Dynamic Host Configuration Protocol (DHCP).
- Hot Standby Router Protocol (HSRP).
- IEEE 802.1q.
- IEEE 802.1x.
- Inter-Switch Link Protocol (ISL).
- VLAN Trunking Protocol (VTP).
Tags: Network, Security, Gr33n Data
du | sort -n -r
du (abbreviated from disk usage) is a Unix computer program to display the amount of disk space used under a particular directory or files on a file system.
sort is a standard Unix command line program that prints the lines of its input or concatenation of all files listed in it's argument list in sorted order. The -r flag will reverse the sort order.
So here you are how to display the amount of disk space used under a particular directory in a descending order: du | sort -r -n
Notice: The -n makes the sort commant sort according to numerical value.
Tags: Linux, Shell, Gr33n Data
sort is a standard Unix command line program that prints the lines of its input or concatenation of all files listed in it's argument list in sorted order. The -r flag will reverse the sort order.
So here you are how to display the amount of disk space used under a particular directory in a descending order: du | sort -r -n
Notice: The -n makes the sort commant sort according to numerical value.
Tags: Linux, Shell, Gr33n Data
15 July 2006
The Israeli Blind Force
Let's first review the Israeli history of attacking Lebanon:
Tags: Israel, Lebanon, Politics, Gr33n Data
- March 1978: Israel invades to stop Palestinian attacks
- 1982: Full-scale invasion; Israel occupies Beirut; pro-Israel militias massacre Palestinian refugees
- May 1983: Israel pulls back, but keeps "security zone"
- February 1992: Israeli air strike kills Hezbollah leader
- 1996: Israel launches "Grapes of Wrath" raids on Hezbollah; 100 civilians die under Israeli shelling of UN base at Qana
- May 2000: Israel withdraws troops from Lebanon
- January 2004: Prisoners-bodies swap agreed between Hezbollah and Israel
"Furthermore, Hezbollah took the military route. They infiltrated Israel and kidnapped soldiers. They did not kidnap civilians. Israel should not respond with disproportionate force", Saleem Khoury, Beirut, LebanonIsrael has kidnapped so many Lebanese during the last 25 years, so did Hizbollah, so I cannot see any reason for such blind attack towards Lebanon this time. USA for example see that it is Israel's right to do whatever they want to free it's kidnapped soldiers, but on the other hand I also see that it's Hizbollah's right to do whatever they want to free their Lebanese and Arab prisoners in Israel.
Tags: Israel, Lebanon, Politics, Gr33n Data
Juventus, Lazio and Fiorentina to Serie B
Serie A sides Juventus, Lazio and Fiorentina have been demoted to the second division for their involvement in Italy's match-fixing scandal. Juventus were also stripped of their last two Serie A titles and had 30 points deducted, meaning they are likely to stay down for two seasons. AC Milan will stay in Serie A but will start the season docked 15 points. Thirteen of Italy's World Cup-winning squad play for the clubs involved, with five at Juventus.
Source: BBC Sport
Tags: Italy, Soccer, Gr33n Data
Source: BBC Sport
Tags: Italy, Soccer, Gr33n Data
11 July 2006
10 July 2006
Forza Azzurri
Italy finally made it, and won their fourth world cup title. Italy beat France 5-3 on penalties in the World Cup final after the teams finished level at 1-1 after extra time in a dramatic encounter in which French playmaker Zinedine Zidane was sent off. It's really shameful for Zidane to end his football career like that. Anyway, I am really happy to see one of my favorite teams getting their fourth world cup title. They are now just one title behind Brazil. Forza Azzurri !!
Tags: Soccer, Italy, Azzurri, Gr33n Data
Tags: Soccer, Italy, Azzurri, Gr33n Data
09 July 2006
DEF CON Media Archive
DEF CON is the world's largest annual hacker convention, held every year in Las Vegas, Nevada. The first DEF CON took place in June 1993. Many of the attendees at DEF CONs include computer security professionals, "crackers", and hackers with a general interest in computer code and computer architecture. The event consists of several tracks of speakers about computer and hacking related subjects, as well as social events and contests in everything from creating the longest Wi-Fi connection and cracking computer systems to most effectively cooling a beer in the Nevada heat.
DEF CON Media Archive
You may also find other Hackers Convensions here
Tags: Security, Hacking, Gr33n Data
DEF CON Media Archive
You may also find other Hackers Convensions here
Tags: Security, Hacking, Gr33n Data
Coding a Simple Packet Sniffer
This Indian guy has a nice article about writing a simple packet sniffer using C and libpcap. Learning to write a packet sniffer may be your first step in order to write more advanced network security tools, such as IDS's, Network Protocol Analyzers, Firewalls, etc.
Amit Saha's Packet Sniffer
P.S. Geocities is dead and so is the above link :(
Tags: Programming, Networking, Security, Gr33n Data
Amit Saha's Packet Sniffer
P.S. Geocities is dead and so is the above link :(
Tags: Programming, Networking, Security, Gr33n Data
Avoid Symantec Appliances, says Gartner
Companies should avoid investing in Symantec's network security appliances, and should evaluate offerings from other vendors, Gartner has warned. The analyst firm said that it issued the warning because it believes that Symantec is moving away from selling network security appliances as it concentrates on "new business directions". Gartner's advice comes after Symantec told some customers on 23 June that it is winding down development of the Symantec Gateway Security (SGS) and Symantec Network Security (SNS) products.
Source: Vnunet.com
Tags: Security, Symantec, Gr33n Data
Source: Vnunet.com
Tags: Security, Symantec, Gr33n Data
08 July 2006
GMail Web Clips Limitation
One of the smartest moves Google have made, was introducing the so called Web Clips feature to their Gmail. It's simply a news/feeds reader embedded into the Gmail web interface, so you can get the latest news/feeds into your email interface, and on the other hand you'll be bounded more to Gmail. I myself have my Gmail active in one of the tabs of the browser all the time. But, today I've noticed that they have a limit of 40 feeds on those ones you can add on your account. I think they have to increase such limit, or else people may grab another feed aggregator and use it instead.
Tags: Gmail, Feed, Gr33n Data
Tags: Gmail, Feed, Gr33n Data
07 July 2006
Otlob's Approach of Automation
Otlob.com is an online site for placing orders to different fast-food restaurants. As far as I know, the point of having such automated web based tool is to make the ordering of stuff much easier, compared to ordinary phone orders etc. But, it seems that this is not the case with Otlob. I made an order there, but for some reason they were not able to contact the fast-food restaurant. So they called me telling me that my order will be delayed for half an hour. The point is that the order was never delivered, and when I called them they claimed that they asked me to cancel my previous order and make a new one myself after half an hour. Lets assume that they are right, and this is what they really said, however it is not the truth. Let me ask you, what is the point of having an automated tool and orders database, if you are not able to queue the orders yourself instead of asking people to cancel their orders and make new ones later?! What if they were not able to reach me by phone?! I think the problem is when people try to enter the dot-com era with a stone-age mentality.
Tags: Web, Social, Gr33n Data
Tags: Web, Social, Gr33n Data
05 July 2006
Digging an OpenSSH Tunnel
Scott Baker of Perturb has a nice post about creating an encrypted virtual tunnel between two computers or networks using OpenSSH.
Link: OpenSSH 4.3 VPN Example
Tags: SSH, OpenSSH, Networking, Security, Gr33n Data
Link: OpenSSH 4.3 VPN Example
Tags: SSH, OpenSSH, Networking, Security, Gr33n Data
Cisco Wireless Insecurity
A new Cisco security warning reports that the company's wireless LAN management application has "multiple vulnerabilities" including one that lets a remote user log in with a default administrator password.
Source: Network World
Sometimes I feel that Cisco is the Networking's Microsoft, they have the biggest market share, but on the other hand they almost have one or two security vulnerabilities announced every day in their products. I think that those who have an end-to-end Cisco network have to worry a bit about their network reliability and security as well.
Tags: Cisco, Security, Gr33n Data
Source: Network World
Sometimes I feel that Cisco is the Networking's Microsoft, they have the biggest market share, but on the other hand they almost have one or two security vulnerabilities announced every day in their products. I think that those who have an end-to-end Cisco network have to worry a bit about their network reliability and security as well.
Tags: Cisco, Security, Gr33n Data
Is it 1982 all over again for Italy?
Italy - my second favorite team after Argentina - has made it to the World Cup final today. Now, it's time to wait for Portugal to beat France tomorrow, in order to see a final between two teams with almost similar mentalities.
Tags: Italy, Soccer, Gr33n Data
Tags: Italy, Soccer, Gr33n Data
03 July 2006
Futbol, Germany 2006
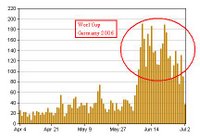
Blog Posts tagged with the word "Futbol" (Spanish)

Blog Posts tagged with the word "Football" (English)
You may notice that in the Futbol tagged posts, they have a higher peak during the worldcup with respect to the rest of the year. However the post tagged with Football are much more, which may be due to that fact that the English sites/blogs are much more than the Spanish ones, also because of that Rugby-clone played in USA which is called football too.
Tags: Football, Futbol, Gr33n Data
Latin Football
Five out of eight teams in the World Cup quarter-final are of latin countries,and now there are three out of four latin countries in the semi-final. I think studies are needed in order to find out what is so special in latin countries, that makes them excel in football. It's also noticed that three teams other than Brazil have brazilian players in them, Tunisia (Santos), Japan (Alex), and Portugal (Deco).
Tags: Soccer, Futbol, Gr33n Data
Tags: Soccer, Futbol, Gr33n Data
Weighted Toys For Your Children
Adding weights to children's toys may help them improve their fitness during playtime, the results of a small study suggest. Various reports have pointed to the benefits of physical activity in helping children maintain healthy body composition and improve cardiovascular and skeletal systems, heart rate, blood pressure and levels of the "good" HDL cholesterol. Studies have also shown that physical activity declines as children grow older. However, there are two issues that need to be explored which are the design and safety of weighted toys and whether children would be interested in playing with them, the researcher noted.
Source: Reuters, Oddly Enough
Tags: Social, Oddly Enough, Gr33n Data
Source: Reuters, Oddly Enough
Tags: Social, Oddly Enough, Gr33n Data
EMC to buy RSA
The acquisition is part of EMC's ongoing efforts to expand from a storage hardware provider into a one-stop shop for storing, managing, accessing and securing data throughout the enterprise, or what EMC calls ILM (information lifecycle management). RSA will operate as EMC's Information Security Division, which will be headed up by RSA President and CEO Art Coviello, and headquartered in Bedford, Mass.
Source: NetworkWorld.com
Tags: Storage, Security, Gr33n Data
Source: NetworkWorld.com
Tags: Storage, Security, Gr33n Data
My CV, Whose CV !?
In today's world people send their CV's by email, rather than ordinary mail or by hand. But I've noticed in most of the CV's I receive, that their file names are "MyCV.doc", "CV.doc", etc. I really can't get the point of calling the file My CV, instead of your own name. It seems that this has something to do with Microsoft's naming conventional MyPhotos, MyProject, etc.
Tags: Common Sense, Social, Gr33n Data
Tags: Common Sense, Social, Gr33n Data
Subscribe to:
Posts (Atom)
